Although the concept of Zero Trust Architecture was introduced several years ago by John Kindervag, VP for Forrester Research, based on the principal of “Never Trust, Always Verify”, it has only recently been gaining popularity in wake of growing cyber-attacks.
The National Institute of Standards and Technologies (NIST) defines cyber-security standards, one of which is SP 800-207 “Zero Trust Architecture“.
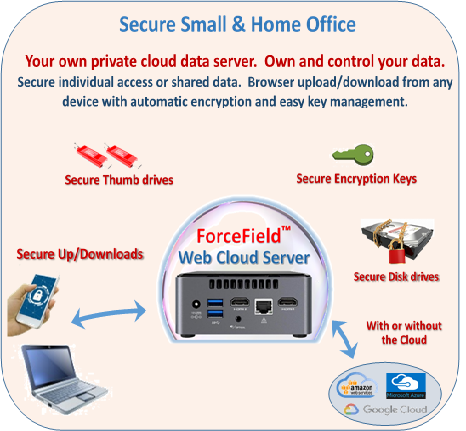
Our Zero Trust Storage™ is based on the Zero Trust Architecture and used in several NIST projects for Data Integrity, Data Confidentiality, and protection of Industrial Control Systems including robotics and audit systems. This security is enforced by hardware so it cannot be bypassed. It is used by NCCoE SP 1800-25 & 1800-11 for “Protection and Recovery from Ransomware and other Destructive Events”.